flag{CTF…WTF?}
CTF 101

Have you always been interested in participating in a Cyber Capture the Flag (CTF) event but you’re not quite sure what to expect or how to get started? This post is a follow up to a talk I gave for WiCyS San Antonio that will provide you with an introduction to these events as well as some tips and tricks I’ve picked up in my own CTF journey.
Experience
In October 2019 a friend of mine encouraged our group to attend Texas Cyber Summit. While there, he also pointed us in the direction of a CTF he wanted to participate in: OpenSOC. Prior to this the only experience I had with CTFs was a DEFCON qualifier I tried in 2017; it was way above my skill level at the time and crushed any confidence I was gaining in my fledgling DFIR skills. Needless to say, I was on the fence about trying another CTF event.
After some convincing I sat there at a table with some of my coworkers after the OpenSOC CTF officially began and immediately felt like I was out of place. I was nervous, I didn’t know how to use the tools (Moloch? Never heard of her), and was watching my friends blaze through the first section like it was nothing. I know firsthand how completely overwhelming these events can be. But after a while I started learning the syntax of the tools, found my footing, and was finally able to get some of the flags myself. One flag turned into two, which turned into three…and I had found my groove. Competing in the OpenSOC CTF at Texas Cyber Summit is a defining moment in my career and one of my favorite memories. My team actually ended up taking first place and we won ourselves some Texas Cyber Summit Black Badges.
Since then I’ve competed in the OpenSOC Camp COVID CTF and Trace Labs Open Source Intelligence (OSINT) CTF, among others.
Summary
This post will cover CTF basic definitions and jargon, major event types, the different question topics and categories you may encounter, some tips and tricks, and, most importantly, how to keep your skills sharp.
Definitions
CTFs, largely speaking, are training events. This is mentioned in the above definition but it’s something I want to highlight. Whether you use them to validate your skills, learn new ones, or a mix of both is up to you. As corny as it sounds the biggest objective is just have fun!
One of the main questions folks usually have is “Who can participate?” Barring qualifiers for certain competitions or other niche situations like the National Collegiate Cyber Defense Competition, CTFs are generally open to the public and anyone can play! At the end of the day these are competitions but that doesn’t mean you should shy away from participating.
Another big question you may have is “What kinds of CTFs are there?” Generally speaking, there are two main categories: Attack/Defense and Jeopardy. However, there are additional event types that I’ll cover later in this post. Though they don’t fit the traditional definition of a CTF, they’re worth mentioning as they can introduce you to different areas of InfoSec and provide valuable training opportunities.
Attack and Defense CTFs
One of the most well-known examples of the Attack and Defend CTF style is Cyber Panoply. Below is a short synopsis from their site:
Panoply is a timed competition event. At the beginning of the competition, common resources are available for teams to scan, assess, and penetrate. To claim ownership of a service, teams must plant their flag, an assigned hexadecimal string, inside the banner of the service. An automated scanner detects ownership changes and awards ownership of the service to the team whose flag appears in the service banner. At random intervals, an automated scoring engine checks the status and functionality of all critical services. If a team has ownership of a functional critical service during a successful service check, that team is awarded points for owning and maintaining a critical service.
I personally do not have much experience with these types of events and tend to gravitate more toward the other major CTF type, Jeopardy style.
Jeopardy Style CTFs
Jeopardy style CTFs are my personal favorite. If you love solving puzzles this is the CTF style for you, hands down.
Mixed/Miscellaneous CTFs & Wargames
“This OSINT CTF is non-theoretical where contestants work in teams of up to 4 members to crowdsource the collection of OSINT to assist law enforcement in generating new leads on missing persons. In the information security community, a typical CTF will be of a technical nature where “flags” are hidden within pre-configured servers/virtual machines that contestants have to obtain using hacking techniques to gain points. The Trace Labs OSINT CTF differs from this by having different flag categories based off pieces of information that law enforcement would look to gather to aid in a missing persons case.”
Unlike a typical CTF that’s time-based, these are persistent and can be completed at your own pace:
- Over The Wire (OTW):
“The wargames offered by the OverTheWire community can help you to learn and practice security concepts in the form of fun-filled games.”
- Hack The Box (HTB):
“An online platform to test and advance your skills in penetration testing and cyber security. Join today and start training in our online labs.”
Question Topics & Categories
These are just some of the topics you may encounter during a CTF. Does this mean you need to be an expert in every single category above? Not at all. Some general knowledge may help; however, it’s not imperative by any means that you’re a SME in any of these. I’ve encountered several situations where I’ve had to just Google-fu my way through some challenges.
Example Challenge Questions
Okay, so you’ve signed up for your first CTF and you’re thinking “Now what?” The following few slides have some example questions on them, but I also wanted to note some important information that you may see:
- Linked Resources: If necessary, the host may include a link to a Google drive or website containing resources required to answer that set of questions.
- Flag Format: Jeopardy style CTFs that require a “flag” to move on to the next question will specify the format your flag needs to be in to receive credit. Usually it’s something along the lines of:
flag{FLAGHERE} - Hints: Stuck? No problem. If a question is particularly challenging you may have the option to spend some of your points on a hint.
- Points: This is how many points you will earn if you answer the question correctly. Usually the more difficult the question the more points you’ll earn.
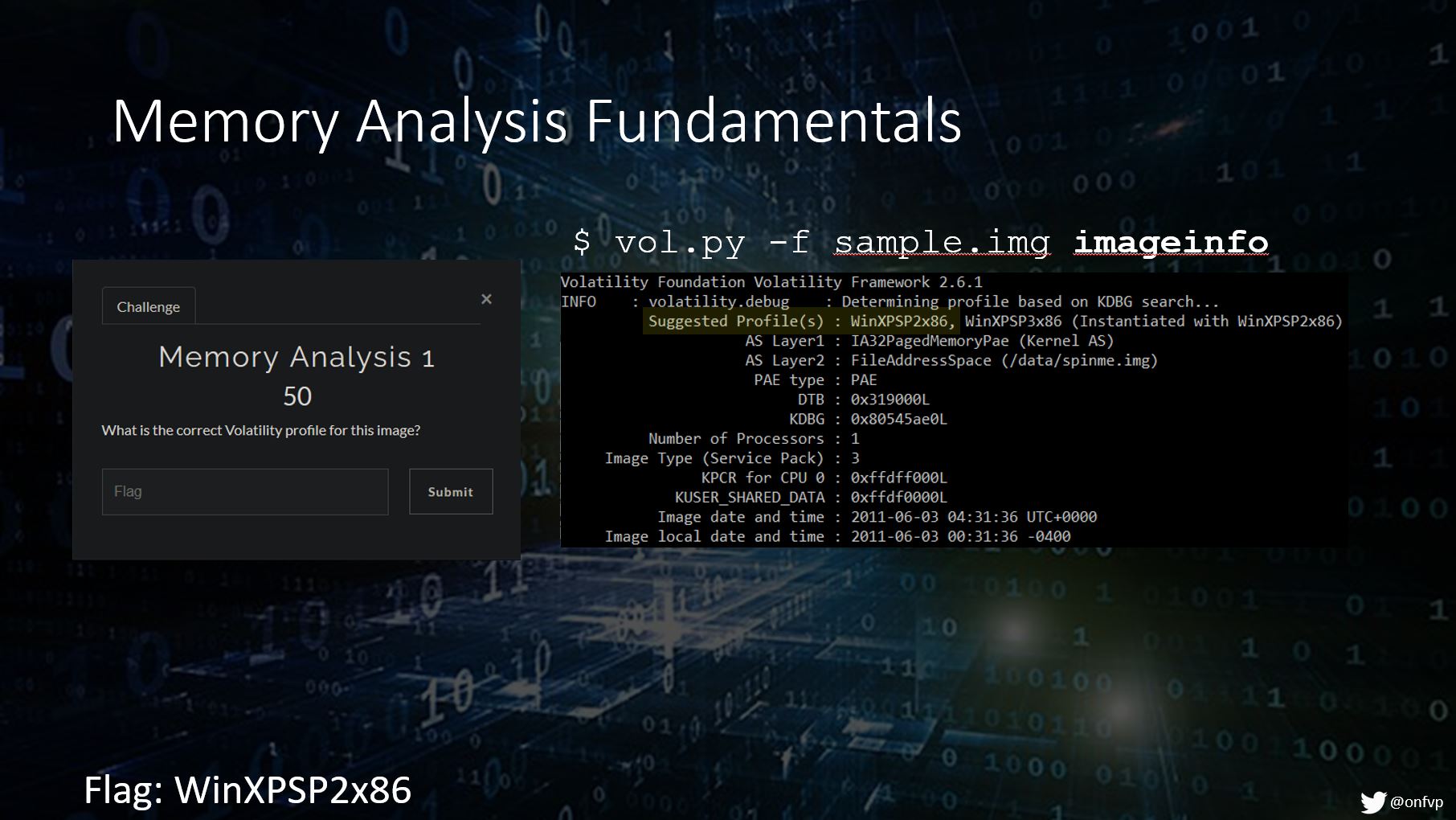
Memory Analysis Example 1
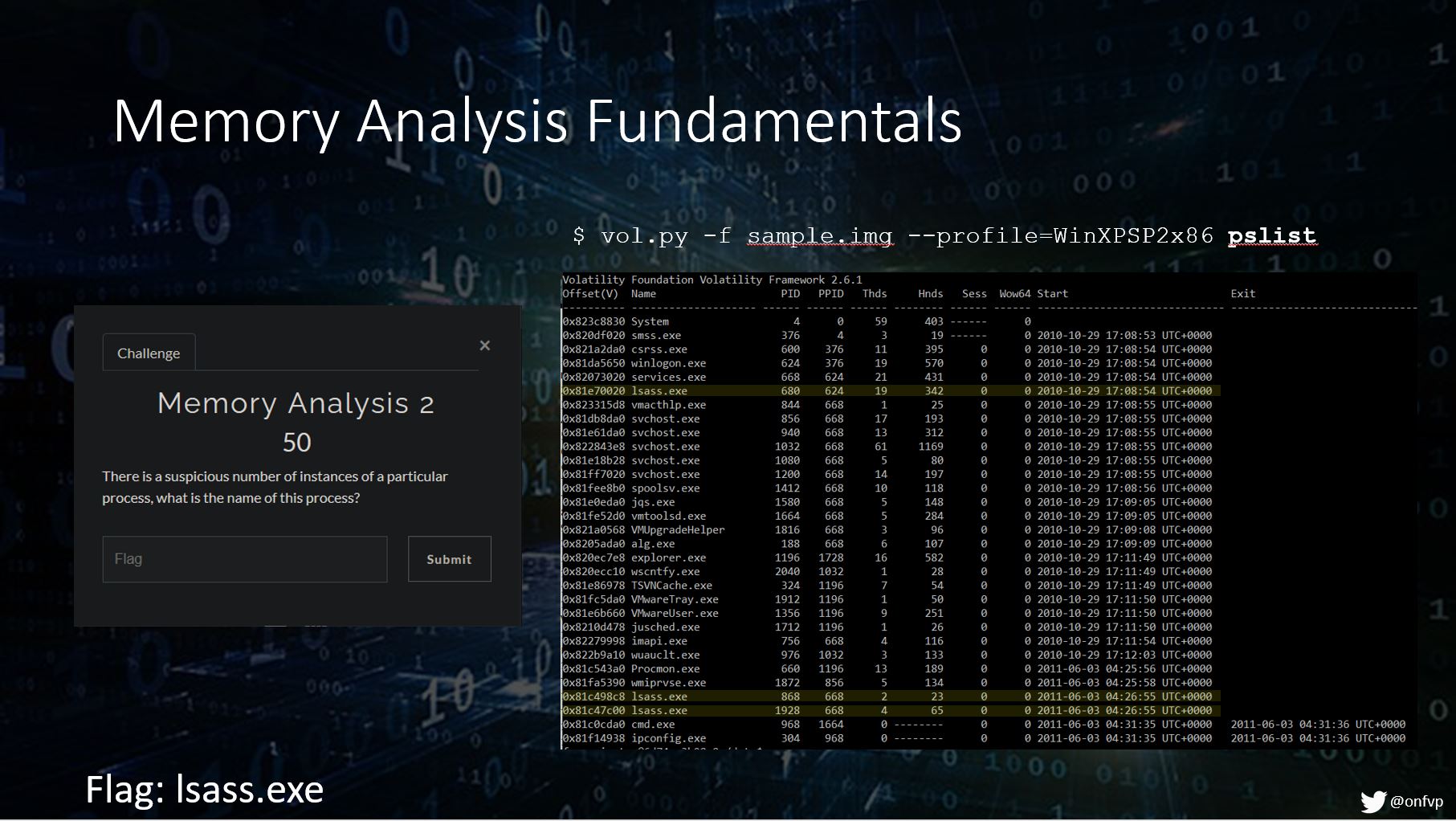
This question and the one below both use a tool called Volatility.
Memory Analysis Example 2
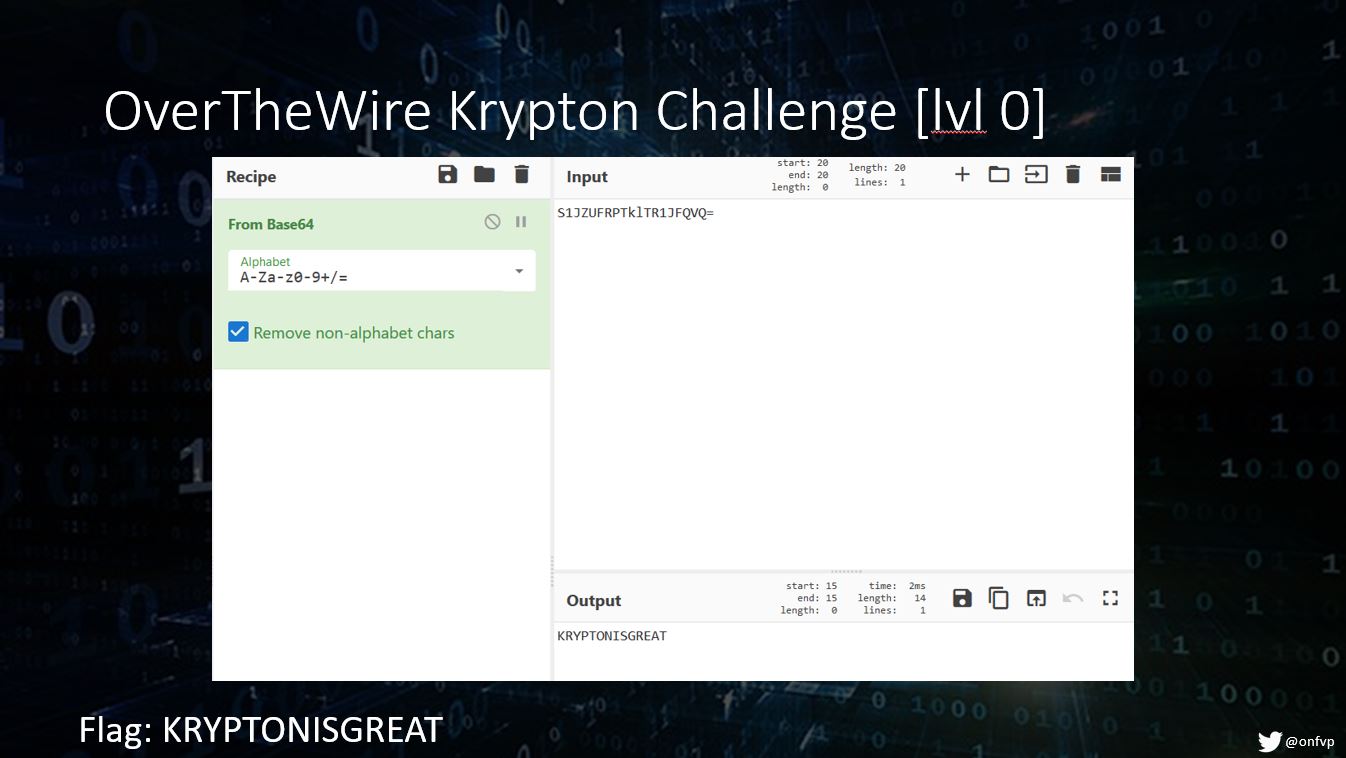
Over the Wire Cryptography Example
The Over The Wire Krypton wargame is a set of cryptography-centered challenges. This slide shows how to take the puzzle initially presented and decode the Base64 string using CyberChef. Other challenges on OTW include *NIX basics, web security, programming, coding, hacking, and more.
Things to Keep in Mind
Now that we’ve covered some of the basics in a CTF and seen some example challenges, here are some things to keep in mind during the event:
- Hints: I touched on this above but if you do want to take hints make sure you communicate with your team. Some teams opt to save hints until the final day or so of the event, and some people don’t mind either way. All that really matters is that your team is all on the same page.
- Wrong Answer Penalties or Limits: Some CTFs will limit the number of guesses on an answer. (This mainly applies to Jeopardy style events). Just take note of this before the event starts especially if you’re a spam-happy answerer.
- This is a training opportunity! Hopefully by now this has been ingrained in your mind.
- Don’t be afraid if your first CTF doesn’t go as planned: It might take a while for you to find a favorite event type or to get used to the questions. Don’t worry! Everyone’s first CTF is a little rough, but I promise you’ll find your niche if you give it time. (Thanks Shoot4Root for the suggestion!)
Keep Your Skills Sharp
There are so many resources out there to forge new skills or hone existing ones.
DFIR Diva maintains one of the most in-depth resource pages I’ve ever seen. She even divides these resources into their respective categories so you can quickly find relevant training to whichever topic you’re interested in.
Did you know that SANS also has a list of free training?
Black Hills frequently hosts webcasts on different InfoSec topics. I’ve attended a bunch of these and have yet to be disappointed.
These are just a few of the places I’ve had luck finding supplemental training and helpful resources. For CTFs specifically you can always Google a category you’re interested in and you’ll easily be able to find writeups from others. I recommend looking at these writeups to see someone else’s thought processes, not necessarily just to find the answers.
Where to Find These Mystical CTFs?
One of the best resources for finding upcoming CTFs is CTFTime. This site maintains a list of events and even lists format (Attack/Defense or Jeopardy), locations, and any relevant notes about the event itself including any prerequisites. There is also a repository of writeups that can be found here. I highly recommend checking out past writeups if you have a spare moment or two.
Sources
- Cisco Blog: “What is a CTF?”
- Trail of Bits CTF Introduction
- Compass Security: Attack/Defense CTF
- Trace Labs
- CTFd: “What is Capture the Flag?”
- atan’s blog: ”What is a CTF and how to get started!”
- Rae Baker: “Finding Missing People with TraceLabs CTF”
- Andrea Fortuna’s Series: “Volatility, my own cheatsheet”